
A Unified Approach to Data Security and Privileged Access
Classify Sensitive Data, Govern Access,
and Detect Anomalies in Real-Time
and Detect Anomalies in Real-Time
Trusted By







Agentless Architecture
Zero Network Reconfiguration
Deploy in Cloud or On-Prem
5 Minute Setup


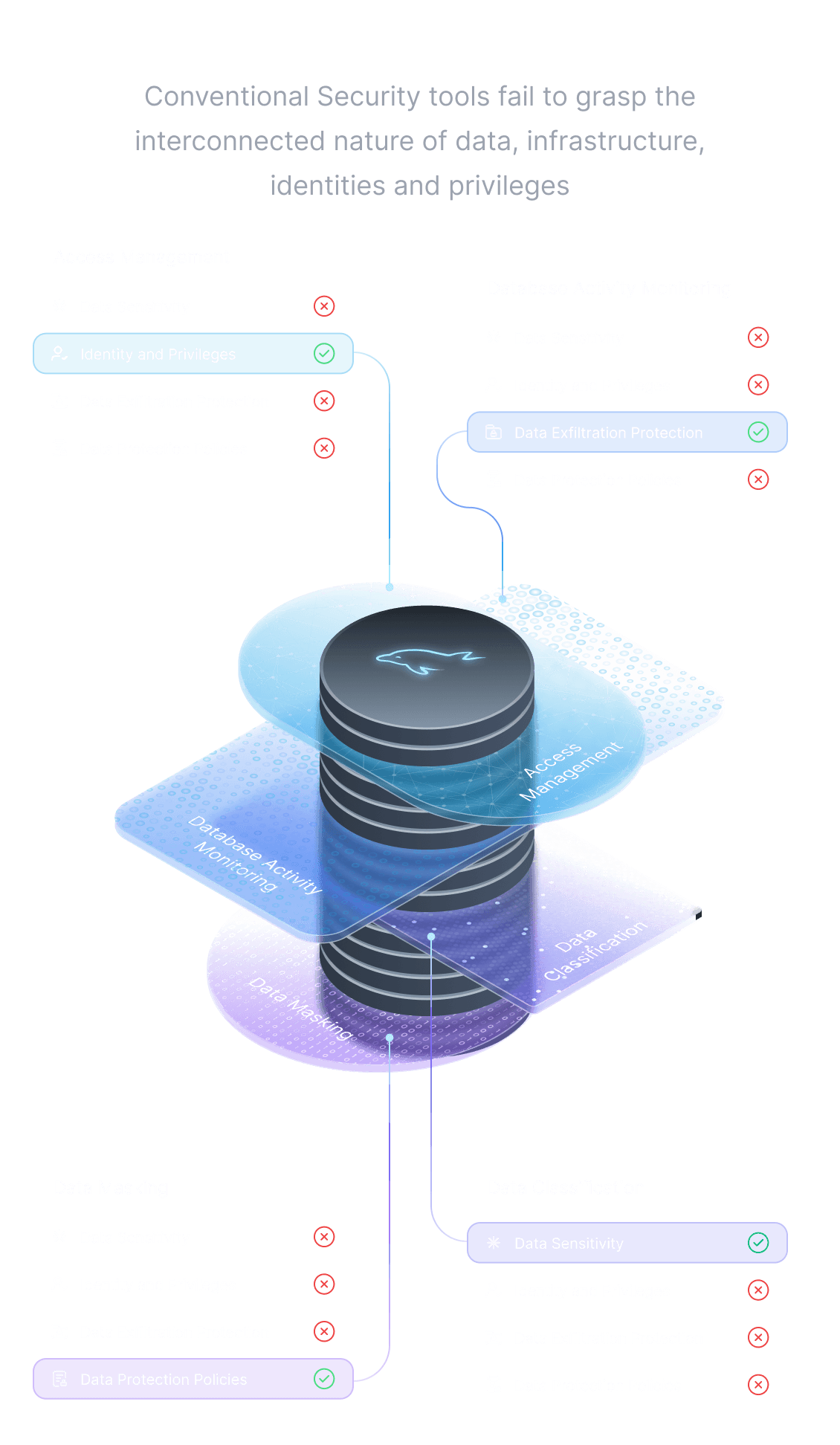
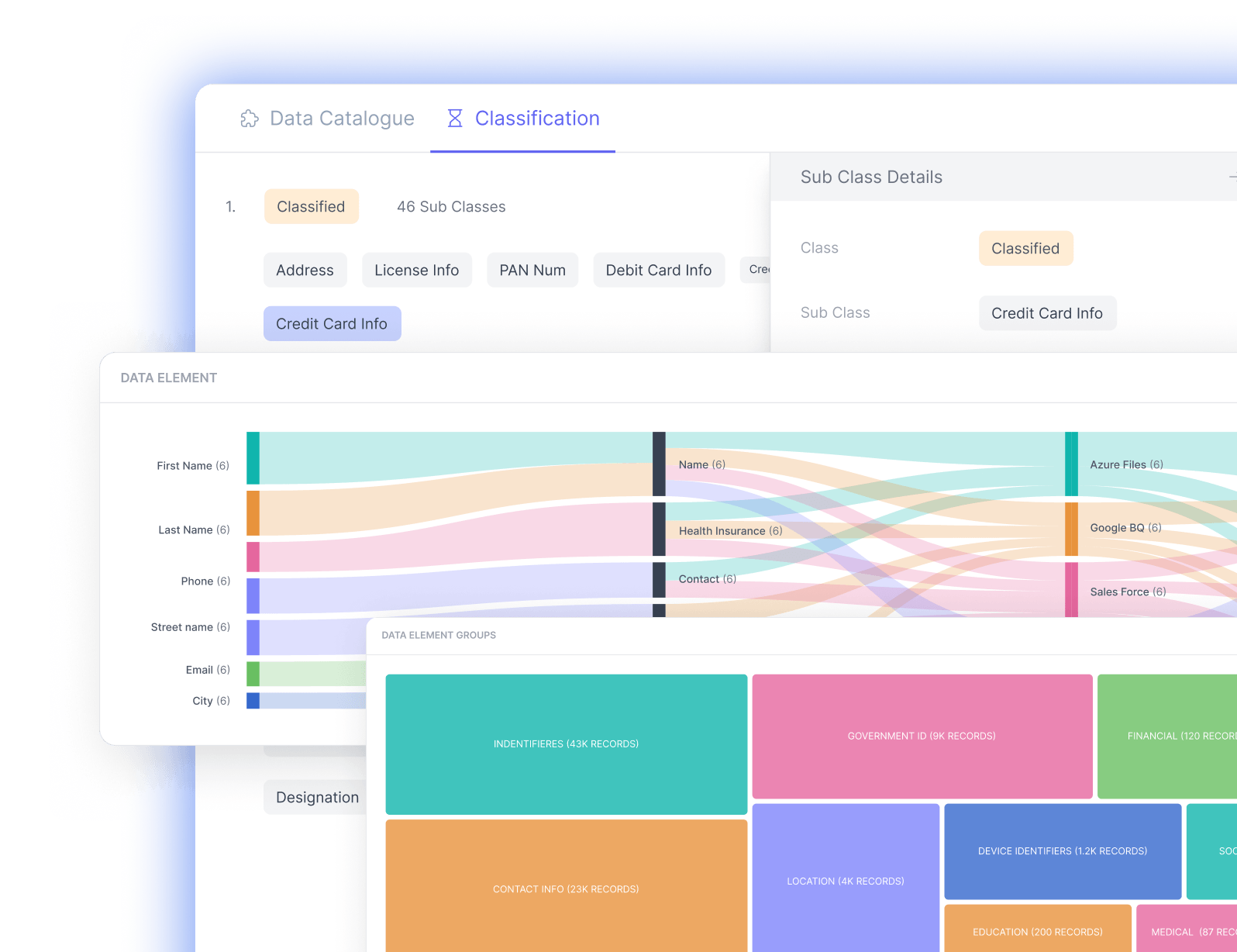
Data Discovery and Classification
More than 64% of financial service companies have 1,000+ sensitive data files accessible to every employee in the organization.
Discover sensitive, classified, and systematically important data automatically, and classify them under different default and customizable labels.
Learn More →
Classify Data under Default or Custom Data Classifiers PII Data
PII Data PHI Data
PHI Data Financial Data
Financial Data Other customizable labels
Other customizable labels

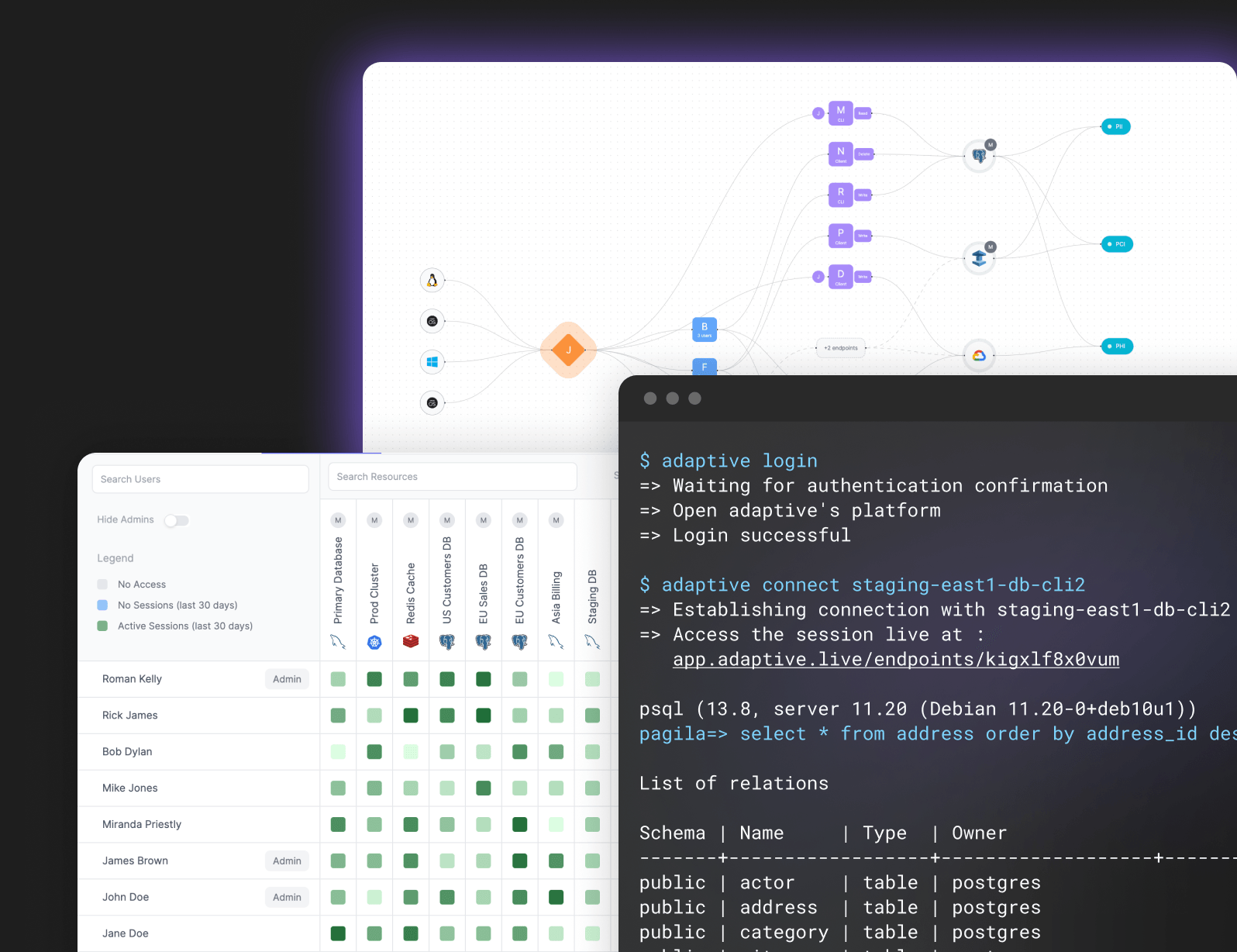
Data Access Governance
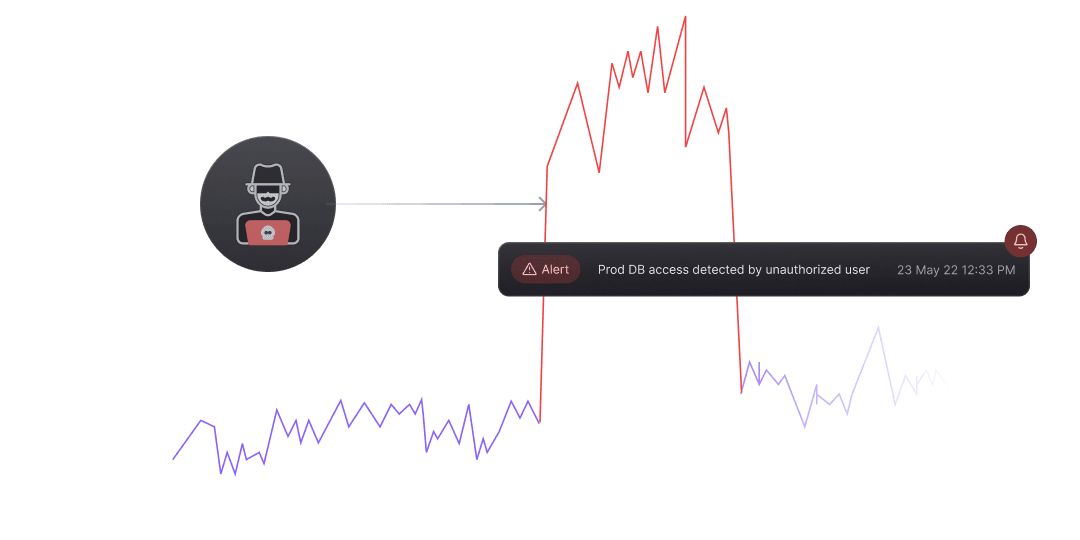
61% of all breaches involve access through credentials, whether stolen via social engineering or hacked using brute force.
Share privileged access to all data sources without sharing the actual credentials. Improve the security posture of your organization.
Learn More →
Just-in-Time Access for all your Data Sources Databases - MySQL, Postgres, etc.
Databases - MySQL, Postgres, etc. Cloud Infrastructure Resources - K8s, VMs, etc.
Cloud Infrastructure Resources - K8s, VMs, etc. Data Warehouses
Data Warehouses Web Services
Web Services

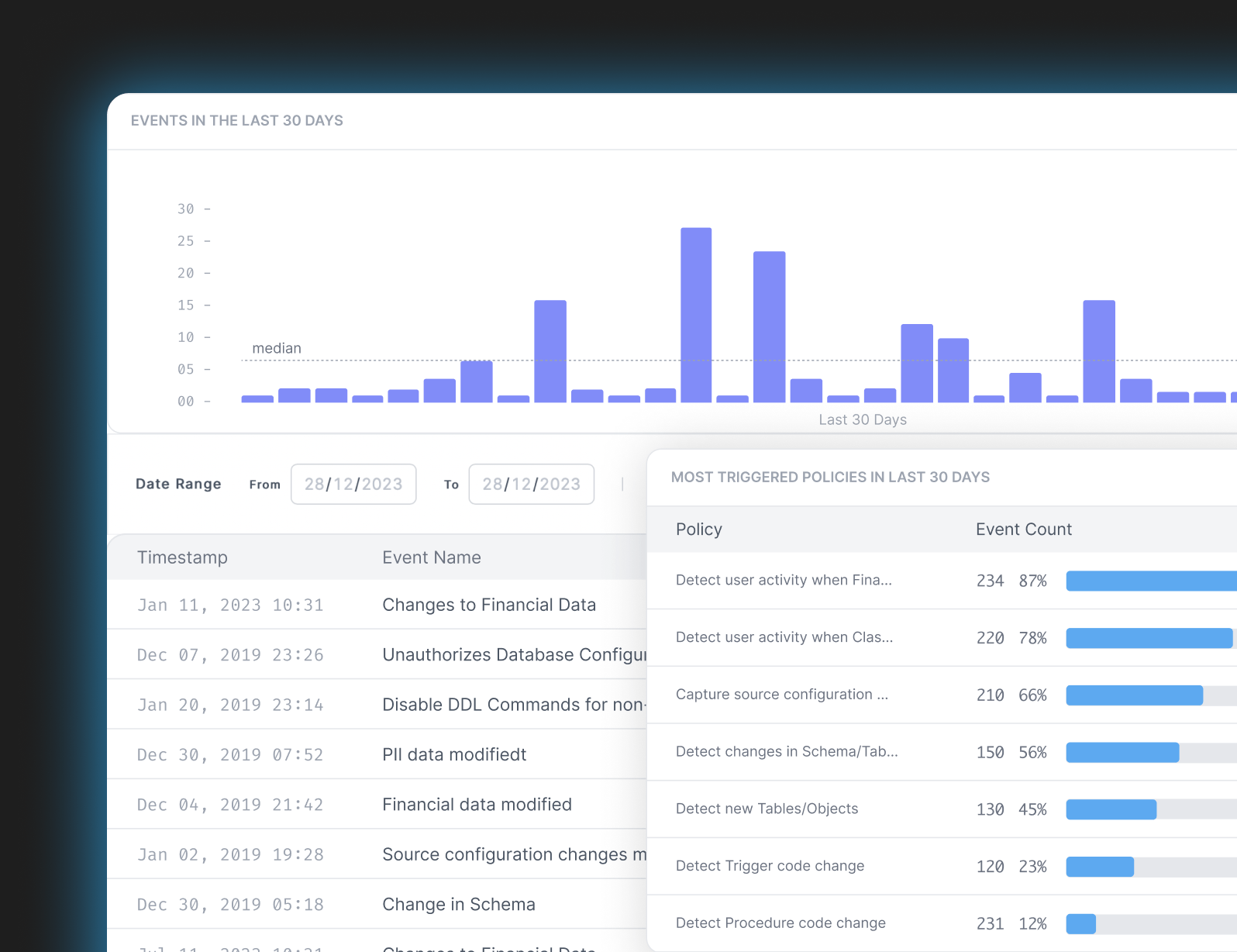
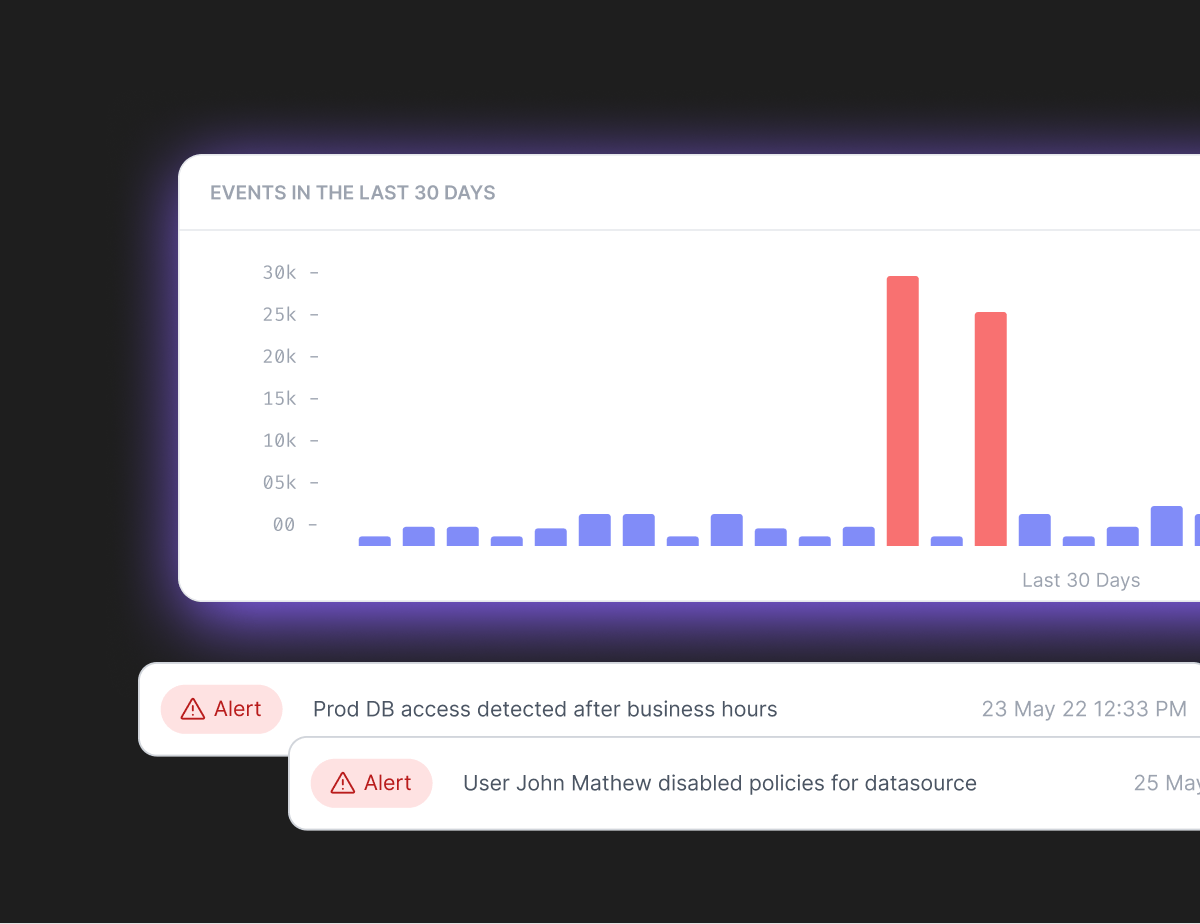
Data Activity Monitoring
$2.3 Million cost difference is observed in case of a data breach for a low compliance failing company as compared to a high compliance failing company.
Continuously monitor and record database activities in real-time with custom policies built in accordance with compliance frameworks.
Learn More →
Detect Irregular Activities based on Policies Data Exfiltration
Data Exfiltration Data Access
Data Access Data Modification
Data Modification Data Deletion
Data Deletion

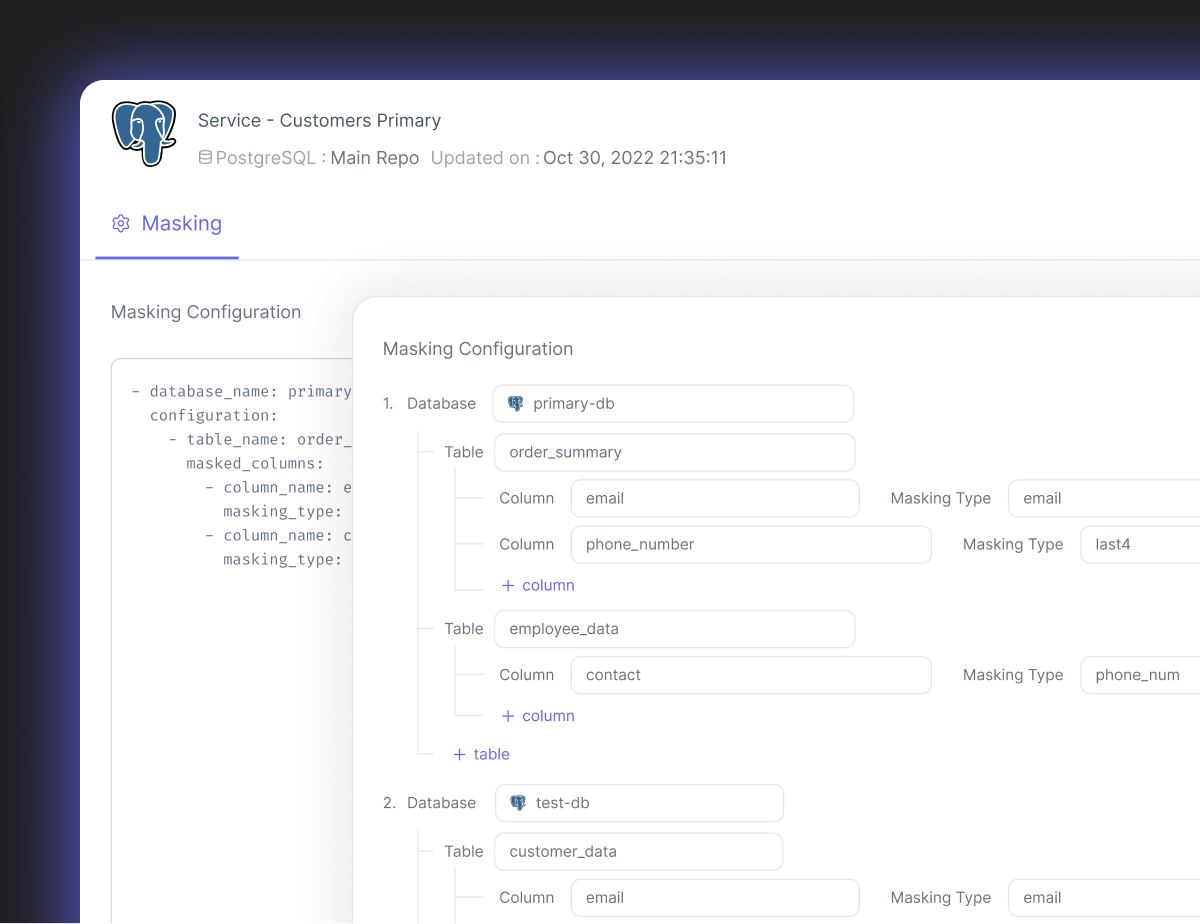
Dynamic Data Masking
Limit sensitive data exposure to any non-privileged users with pre-defined masks to protect data without changing the user's access and workflow.
Learn More →

Anomaly Detection
Identify and alert any unauthorized or malicious data activity transactions and patterns across all structured and semi-structured data sources.
Learn More →

Terraform Provider
Use Terraform to provision and manage access and authorizations

Authorization Privileges
Efficiently manage authorization with dynamic role-based access control

Auditability
Enable identity-based audit trails across all resources

Request-Approval Workflows
Request and approve resource access seamlessly via Slack, Teams, or email

SSO and Directory Sync
Sync users directly from all SSO providers, like Google, Okta, etc.

Compliance-enabled Policies
Enable policies to stay compliant with standards like GDPR, HIPAA, etc.

Enterprise Grade
A new paradigm for Data Security
Agentless Architecture
Zero Network Reconfiguration
Deploy in Cloud or On-Prem

Built for
Regulated Industries
Stay on top of evolving industry regulations with automated audits, data governance policy, access control and other data security measures.
Secure All Your
Data Sources


Comprehensive Data Security Stack for Regulated Industries
 SOC2 Type II
SOC2 Type IIProduct
Use Cases
Industries