7 Alternative Use Cases for a Bastion Host

What is a Bastion Host?
A Bastion host allows authorized users to access a private network through an external network, such as the internet. The bastion host becomes the sole ingress path to those internal resources when it is placed outside the firewall or in a DMZ. Access control is made simpler to monitor while reducing the attack surface.
How to create an AWS Bastion Host?
Below are the brief steps showing how to set up an AWS Bastion Host for your infrastructure.
- Set up a new server to be used as a bastion host.
- Configure firewall rules on the server to allow inbound SSH connections from the internet.
- Configure firewall rules on all other internal servers to allow inbound SSH connections from the bastion host only.
Primary Use Case of Bastion Host
Secure Remote Access is the main use case of a bastion server.
The bastion host is located on its own private subnet and has an organization-facing/internet-facing IP address. Only the organization’s IP or allowed address ranges are accepted by bastion for incoming connections. Access from the bastion to the protected subnets is restricted by the rules specified in the ACLs, allow lists, and other network-level access rules. This adds an additional layer of security.
However, there are multiple ways you can re-purpose the same bastion host to serve multiple use cases. We explore a few of them below.
Alternative Use Cases of Bastion Host
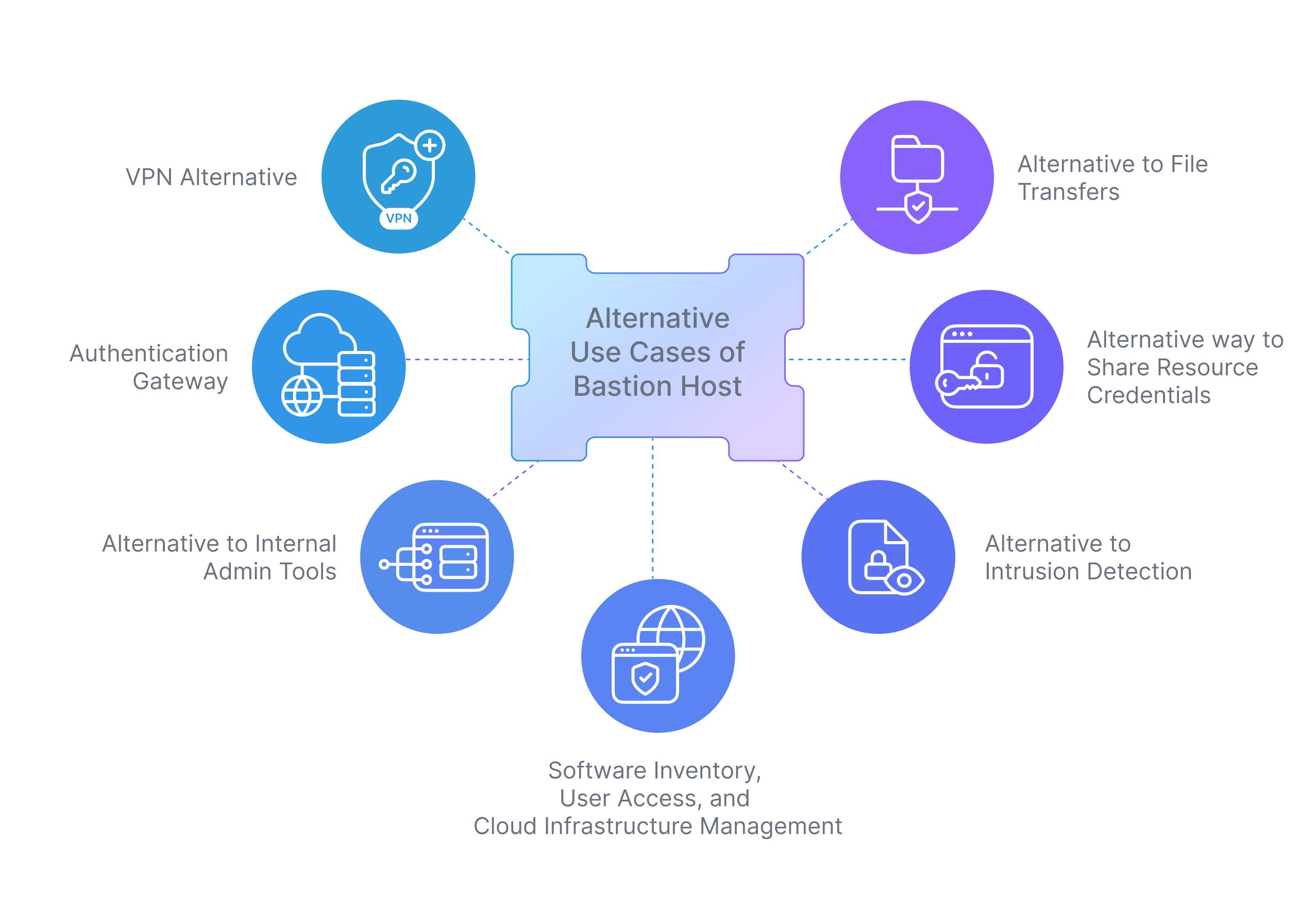
Use case 1: VPN Alternative
Virtual Private Networks are a dwindling technology in recent times. It was established, to connect remote centers of an organization to a centralized data server through a network, most commonly the internet.
An ingenious ‘secure-parameter’ solution to offer a few trusted employees, contractors, and third-party personal remote access to the system, the usefulness of VPNs decreased as the organizations’ infrastructure was decentralized, cloud-enabled, and remote-working was established as a prominent working method. Nowadays, most employees hit the VPN gateway for remote access exposing the gateway’s presence over the internet, to anyone running a scanning application. Increased visibility translates to increased threats. A simple patched VPN appliance undermines the infrastructure, putting the security of the organization at a risk.
To combat the weaknesses of VPNs, organizations have started searching for secure alternatives and Bastion hosts are gaining widespread popularity as an alternative to VPN.
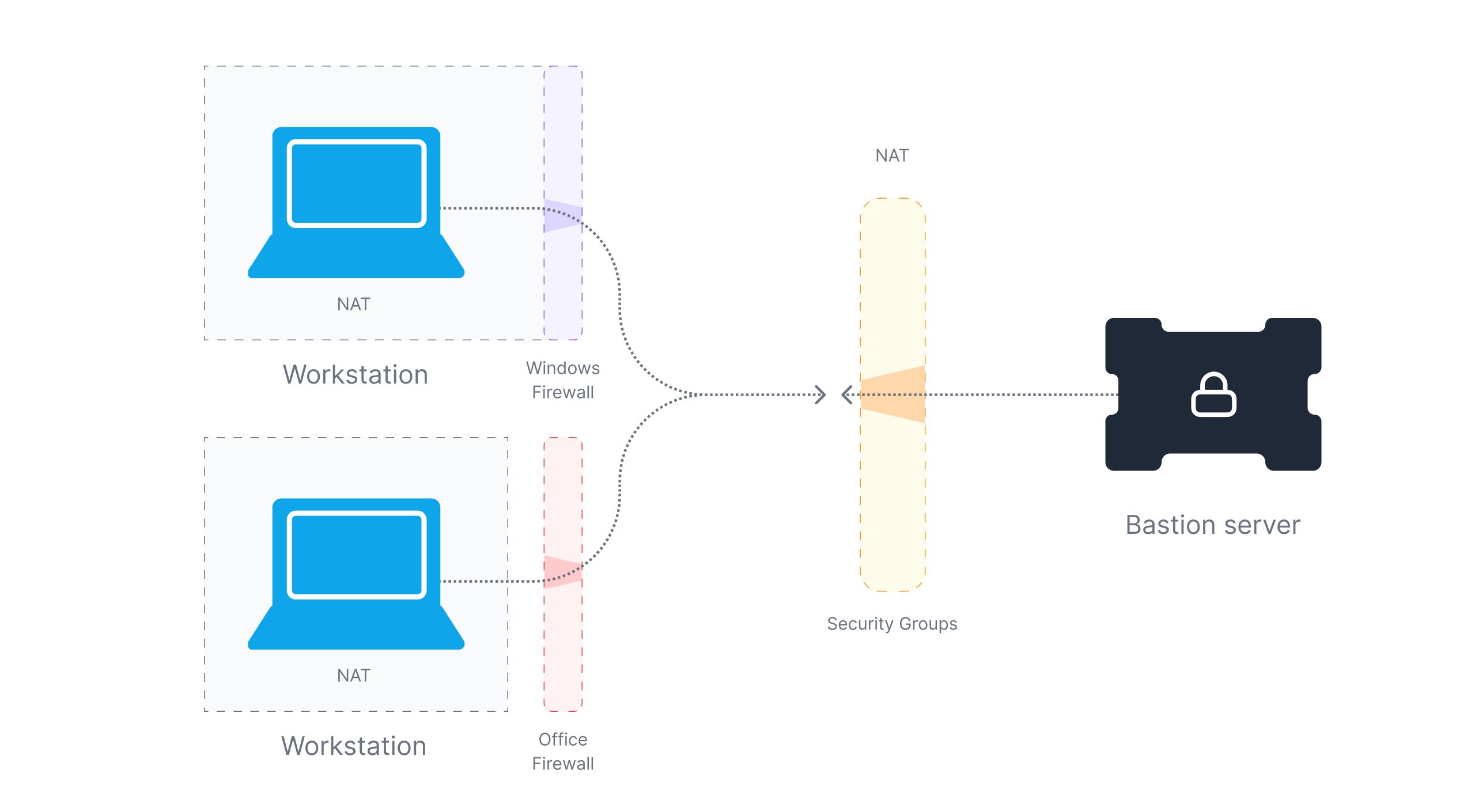
One of the downsides of a bastion host is that you might have to expose the server to the internet. This can lead to the port knocking issue, where various random requests on the SSH port (standard or non-standard) are received. To prevent this, organizations might again need to use a VPN to protect it. Another way to prevent this is to use an outbound-based reverse tunnel.
The benefit of reverse tunneling is that it allows a user to connect peer-to-peer as compared to a VPN where you have to give access to a subnet. You can utilize that already existing connection to create a new connection from your local computer back to the remote computer via reverse SSH tunneling. Other tools that can be used to achieve this are ngrok, SOCKS5, and Adaptive.
Use case 2: Authentication Gateway
It is a security mechanism that is used to manage access to a private network by authenticating and authorizing users before allowing them to connect to the bastion host.
Implementing this paradigm is easy after setting up the reverse tunnel. The gist involves setting up an authentication service (commonly called a gateway) on the Bastion Host. The gateway must be configured to handle services of user identification, authentication, and authorization. Of course, the reverse tunnel has to be established following the steps described in the previous sections. Make efforts to note the outbound port of the gateway, as this is the destination port for the host.
This sets up a secure layer of abstraction where remote clients should first connect to the Bastion Host using SSH and only after they are authenticated by the gateway can they access the server. Ensuring that only authorized users can access the servers, ensuring that data breaches and device-patch breaches prevalent in VPNs are prevented.
The pattern offers a reverse proxy to reroute or redirect requests to the endpoints of your internal microservices. For client applications, an API gateway offers a single endpoint or URL, and it internally routes the queries to internal microservices. By obscuring some implementation details, a layer of abstraction is created. On top of the backend service, more features can be added, such as request and response transformations, endpoint access authorization, or tracing.
Use case 3: Alternative to Internal Admin Tools
The core use case of using Bastion is that it can route multiple users through one host into various downstream resources. In large organizations, instead of giving full-scale access to the downstream resources, access to various scripts is given to users who can execute tasks like restarting a service, cleanup disks, etc.
A Bastion host can be used as an internal admin tool to provide a secure and centralized point of access for administrative tasks across the infrastructure. This approach can help improve security by reducing the number of entry points into the infrastructure and providing greater control over administrative access.
How does it work?
- An admin needs to install an execution engine in the Bastion. It could be python, ruby, lua, PHP, or bash.
- Once the executors are installed, you can persist the operations or internal scripts in the Bastion. Either you can manually upload it in the Bastion or you can set up a git repository that can be cloned and fetched.
- You can create an ACL on the scripts with
chmod,chown, orchgrpwhere in you can specify if the user Alice can only execute scripts to restart DB but not restart the server. - Enable SSH audit to capture logins.
- It is difficult to audit what scripts were executed by whom unless the history is also being captured and logged.
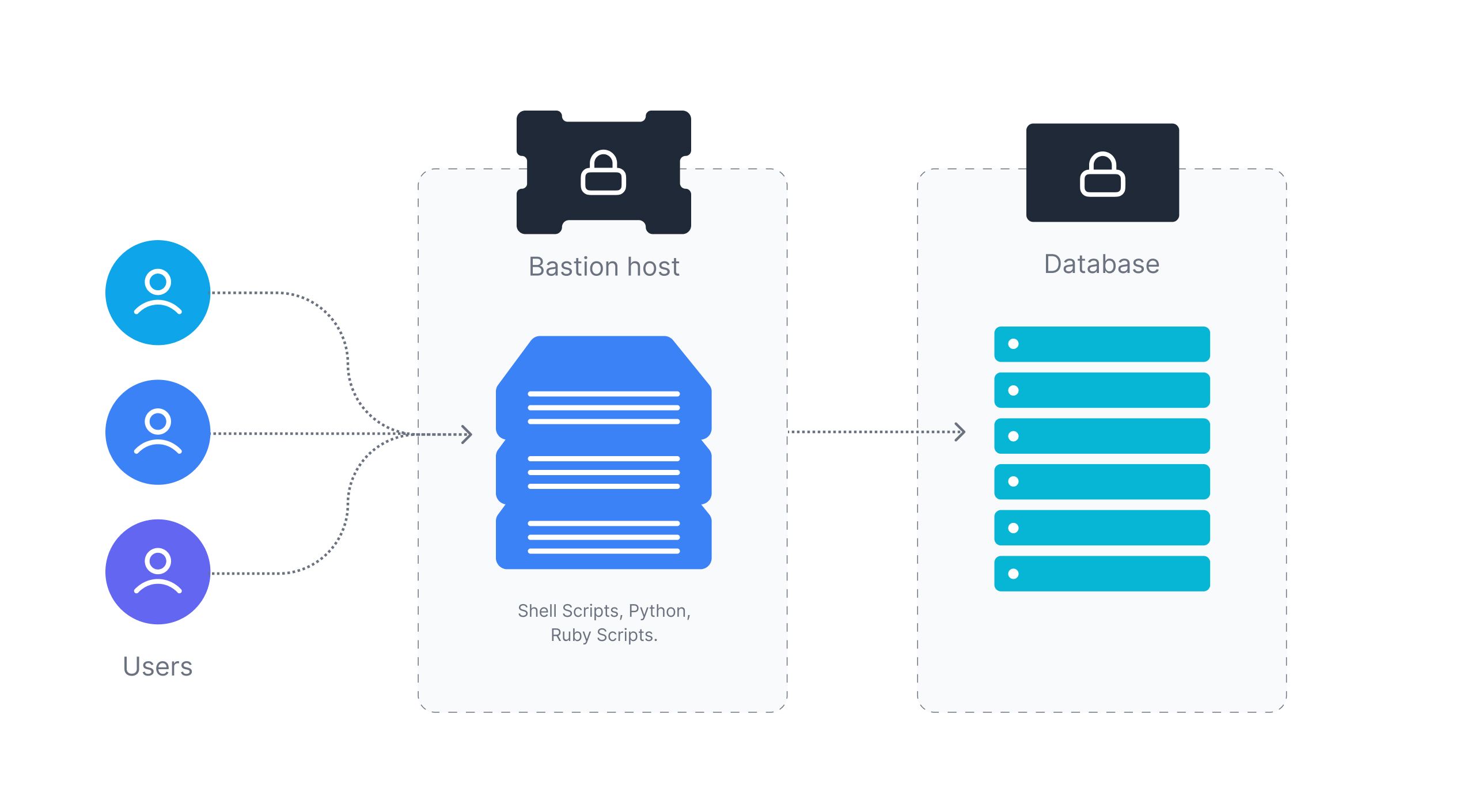
Centralizing administrative tasks and scripts lead to higher productivity gain and a better security posture by reducing the number of entry points into the infrastructure.
Use case 4: Alternative to File Transfers
Sharing huge files between teams and different stakeholders securely is often a challenge. One can use public cloud drive services for non-sensitive data, however, for sensitive data, a Bastion host can be an excellent candidate.
How does it work?
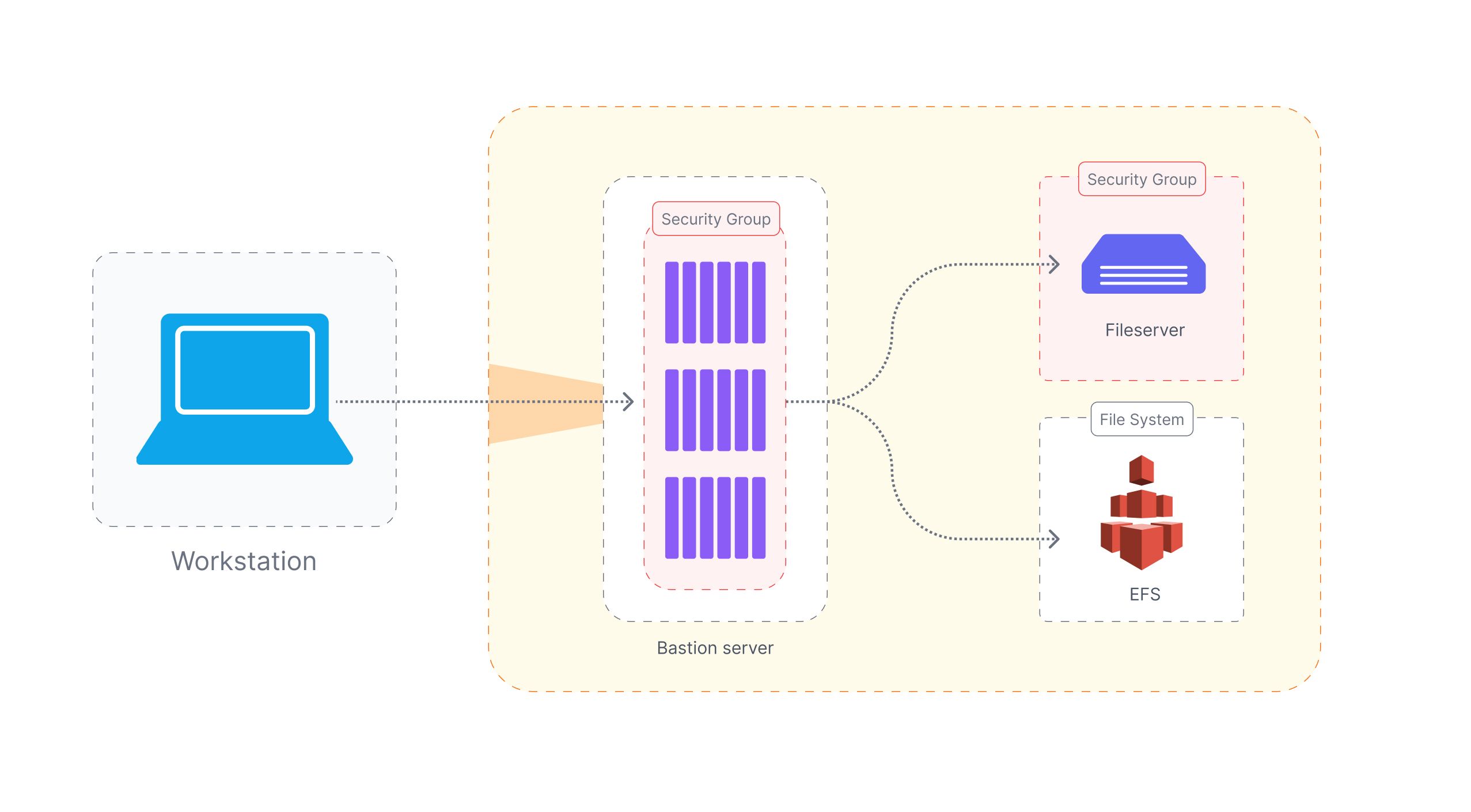
An admin has to install a secure file transfer service such as SFTP, SCP, or FTPS. The Bastion host should be configured correctly e.g. the firewall allows appropriate incoming traffic.
With Bastion host, you can ensure authorized users can only access the files uploaded in the host via sftp service. You can ensure this by creating users for accessors and enforce fine-grain control via chmod and chown. Users can transfer files using scp or an equivalent file transfer service that is configured in the bastion host.
One of the benefits of this setup is that monitoring and audit logs of the file transfers are available by default and can be found in the ssh audit logs.
Use case 5: Alternative way to Share Resource Credentials
One can share resource credentials with bastion hosts by simply saving the credentials in the bastion host itself. As the organization’s downstream resources are protected by the Bastion and cannot be accessed outside the Bastion. It is ok to do this. This method has the following challenges -
- Credential rotation becomes painful as it has to be manually updated
- Keeping track of what credentials are where in the bastion is fairly challenging
- Users do see the real credentials
A better approach to sharing credentials via Bastion is via installing and configuring a secrets management system.
With a secret store, administrators can upload the credentials in the store. Configure a user in the bastion host that can authenticate with the secrets management system and retrieve the credentials. You can grant access to the user configured in the bastion host. Once retrieved, accessors can use this credential to access the downstream resource.
Overall, this improves the security posture of an organization as it makes lifecycle management and rotation fairly easy. But, there is still some risk wherein the actual credentials to access the resources are still exposed.
Use case 6: Alternative to Intrusion Detection
For this use case, the organization has to first install an intrusion detection system.
There are two ways Bastion can help with intrusion detection.
- Install and configure intrusion detection software: You'll need to install and configure intrusion detection software, such as Snort or Suricata, on the Bastion host to monitor network traffic and detect potential security breaches.
- Configure the Bastion host firewall: Ensure that the firewall on the Bastion host allows incoming traffic on the appropriate ports for the intrusion detection software.
- Configure the intrusion detection rules: Configure the intrusion detection rules to detect the specific types of activity that you want to monitor.
- Monitor network traffic: With intrusion detection software in place, the bastion host can monitor network traffic and log any suspicious activity.
- Set up alerts and notifications: Configure the intrusion detection software to generate alerts and notifications when potential security breaches are detected so that administrators can take appropriate action.
- Investigate and respond to potential security breaches: When potential security breaches are detected, investigate the activity and take appropriate action to prevent further damage.
Additionally, organizations can use it as a honeypot for trapping hackers.
You can purposely expose the port so that it gets knocked by intruders. Collect their IP addresses and add them to the blacklist.
Use case 7: Software Inventory Management
In an organization, it is essential to maintain an up-to-date software inventory and dependencies in order to maintain a good security posture and manage critical vulnerabilities. Unauthorized access often exploits an old and known vulnerability to gain access to various IT systems. A bastion host can play an important role in software inventory management as it has access to various downstream resources. A software inventory management system on bastion can be set up as follows:
- Install and configure an automation platform like Ansible, Puppet, or Chef, on the bastion host to manage software and user access across the infrastructure.
- Allow outbound connections on the firewall so that the software updated can be downloaded from repositories. If the repositories are hosted locally or are known to users, then whitelist them.
- Run the automation script to scan the software services and databases and check if they need an update.
- Schedule the automation via cron job for daily, weekly, monthly, or quarterly scans and updates.
A bastion host can be used to streamline the management process and improve administrator overview over software updates. These processes help organizations achieve compliance and regulatory best practices without compromising productivity.
Conclusion
As a work-from-home enthusiast, it is increasingly clear that the current workforce prefers remote working. As the shortcomings in VPNs become more apparent, organizations are searching for secure alternatives and Bastion Hosts have emerged at the forefront. From being a projection of a castle in ancient times to a part of the IT infrastructure of many organizations currently, the humble 'Bastions' are used where they are seen fit, and rightly so. The ease of configuring and deployment makes it popular.
Although Bastion Hosts have many use cases, they tend to remain independent of each other. Configuring a Bastion host for an authentication gateway and implementing it in an existing IT infrastructure differs greatly to file transfers. There is also an inherent reliance on SSH which can be targeted by attackers.
If only there was a platform that can present the above-mentioned use cases of a bastion host easily and securely, organizations can get broader use cases with tighter security into their servers!


 SOC2 Type II
SOC2 Type II