IAM isn’t enough to protect your resources

Introduction
In 2018, Tesla’s internal systems were maliciously tempered with by an employee who, despite not being in a top-level position, had been granted extensive access. This rogue employee altered the company’s manufacturing operating system and exfiltrated confidential data, causing considerable damage to the company. The unchecked infrastructure access and unmonitored access patterns led this employee’s malicious actions go undetected.
In a way, the 200 fully featured resources offered by AWS and made accessible through it’s Identity and Access Management (IAM) platform are susceptible to a similar vulnerability. IAM is a foundational security platform for an organization’s AWS resources, but is isn’t sufficient for all of its security requirements.
While IAM is very flexible and enables organizations to effectively manage resource access, to ensure security and faster incidence response, organizations need to define granular roles and provide Just-in-Time (JIT) access while monitoring all user activity and recording logs as they happen.
Privileged Access Management (PAM) does exactly that. Where IAM can be used to define more high level roles and grant access to resources, PAM can be used to grant JIT access to resources which limits the user actions. Neither IAM nor PAM is superior, they both serve different purposes and it is important to understand each, and how they play crucial roles in the overall security posture of your organization.
What is AWS IAM?
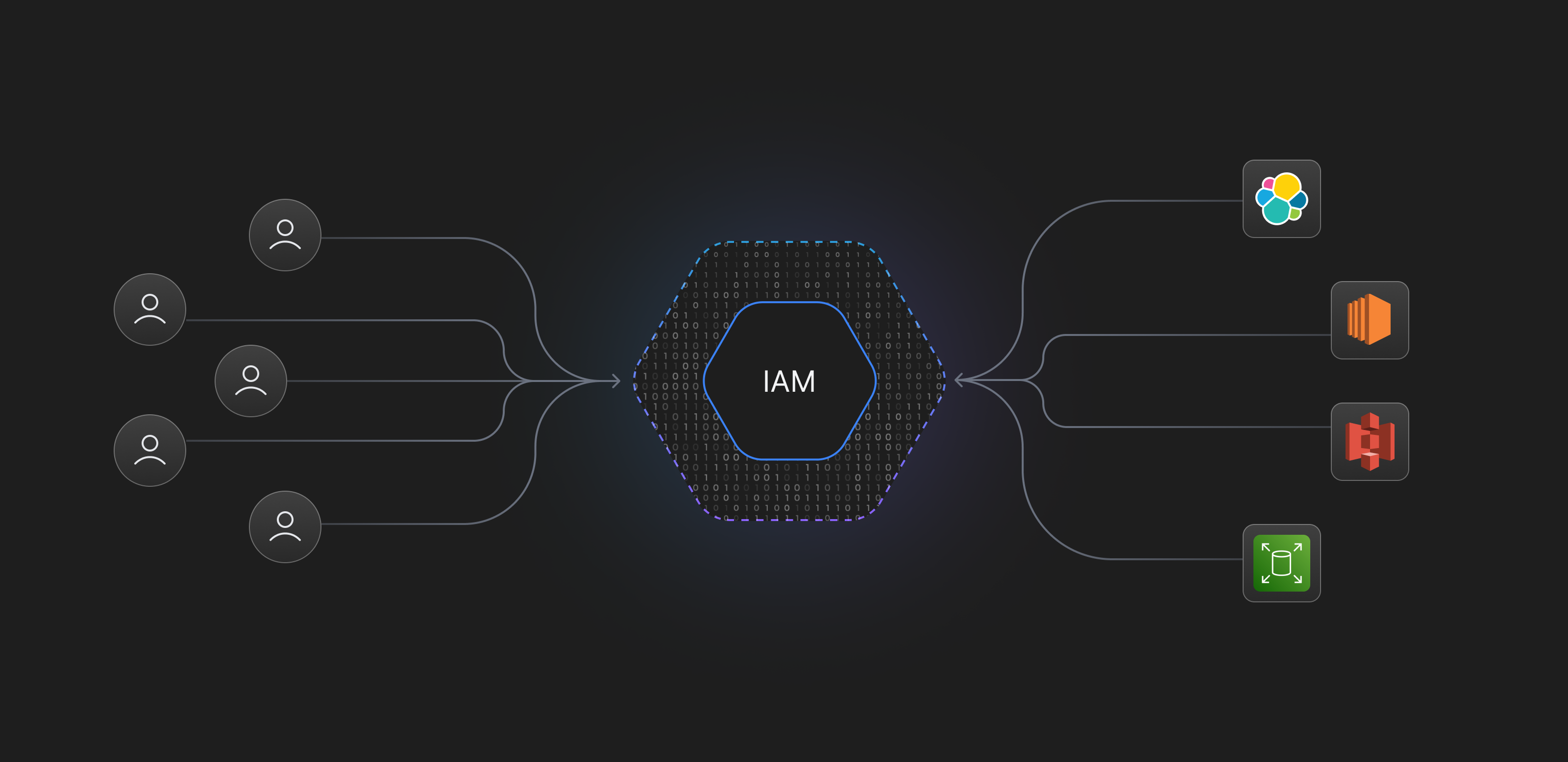
AWS Identity and Access Management (IAM) is a web service that helps you securely control access to AWS resources for your organization. It enables you to manage users, security credentials such as access keys, permissions that control which AWS resources users and applications can access, and policies that define what they can do with these accessed resources. IAM is a crucial component of AWS security, providing the tools to maintain secure access to all its services.
Without IAM, all AWS resources can be accessed only by the root user, and access to new users can only be extended by sharing credentials. All users at all times will have full access to all the subscribed resources, creating a wide attack surface.
What are the characteristics of IAM?
All of IAM’s characteristics can be boiled down to two things—
Centralized Access Control
IAM provides a centralized platform for managing access to AWS resources. It allows for the definition and enforcement of access policies for users, groups, and roles, ensuring that only authorized individuals or entities can access specific resources.
The system adminstrator can choose from standard policies or define their own. These policies ensure that the user can only access what is made accessible to them.
Role Based Access Control (RBAC)
RBAC is a simple and effective way to manage users. The median size of an organization that uses AWS is 8000 FTEs and defining and managing users on a large scale becomes complex if the admin has to individually configure access all the time.
IAM let’s the admin define roles and configure policies on it. Any user assigned to the role will automatically inherit all the privileges from the role.
Why isn’t IAM enough?
IAM systems are foundational to securing organizational resources by managing user identities and controlling access to resources. They enable administrators to define roles and permissions with a level of granularity that seems sufficient for general access control. However, when it comes to protecting the most sensitive assets and ensuring a robust security posture, IAM alone falls short.
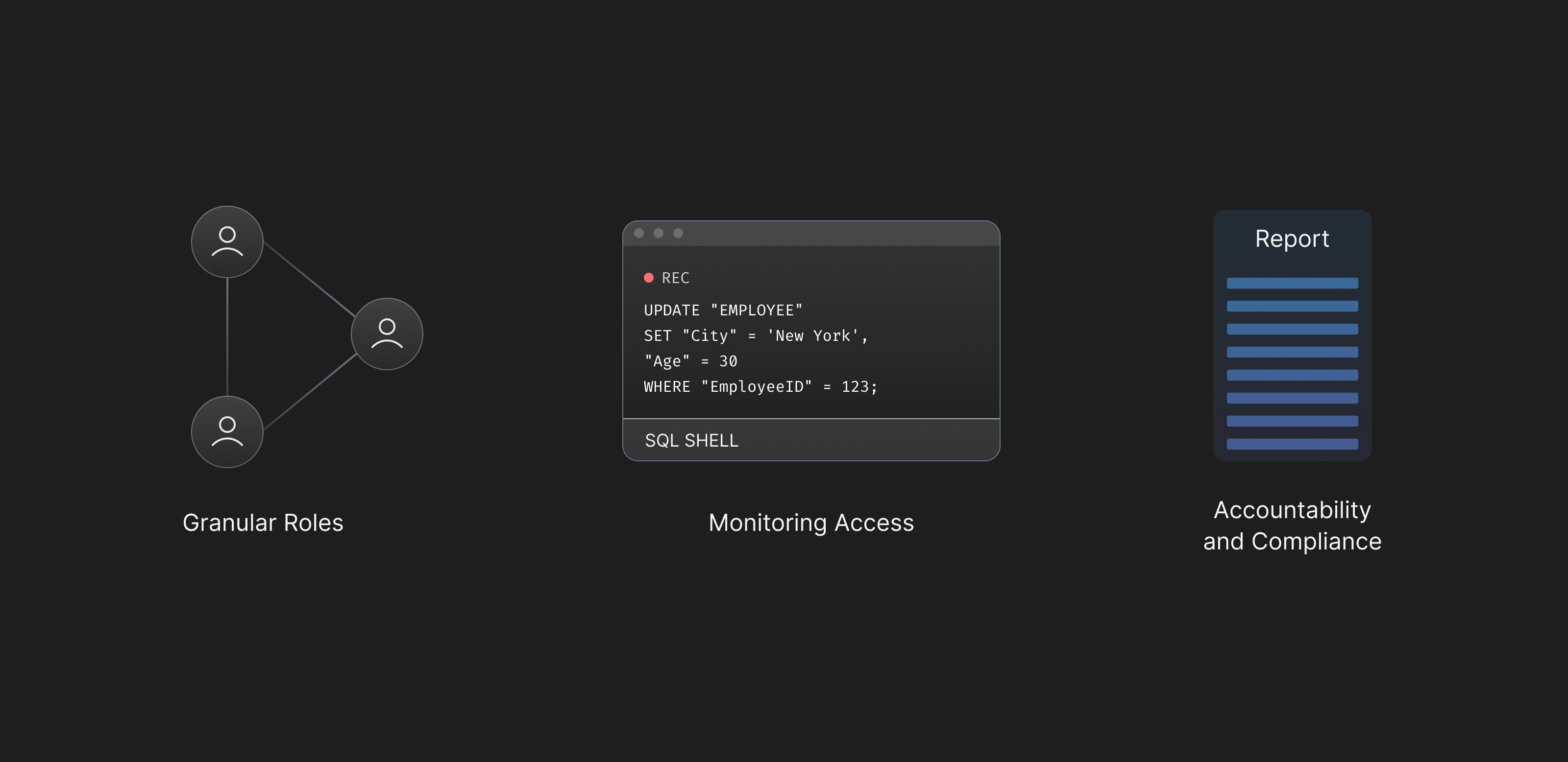
Granular Roles and JIT Access
IAM provides a framework for role-based access control (RBAC), allowing defining user roles and permissions that control access to resources. This model is effective for general access management but lacks the depth required for managing access to highly sensitive or critical resources.
For instance, IAM can restrict access to an S3 bucket but will fail to control access to specific objects or data within that bucket. The static nature of IAM roles do not cater well to the dynamic access requirements for the modern cloud-native world. There's a growing need for Just-In-Time (JIT) access provisioning, which grants users temporary access to resources only when needed and revokes it immediately after. This approach minimizes the risk window but requires a level of dynamism and granularity beyond what IAM offers.
Access Logs and Real-Time Monitoring
While IAM provides logging capabilities, it isn’t sophisticated enough for real-time monitoring and analysis of access patterns. Effective security posture management requires not just logging access events but also analyzing these logs in real time to detect anomalies or unauthorized access attempts. IAM logs can tell you who accessed what and when, but they might not provide the actions performed by the user which can limit the response capabilities.
Accountability and Compliance Gaps
IAM plays a crucial role in establishing accountability by tracking user activities and access patterns. However, for organizations subject to stringent regulatory requirements, IAM's capabilities might not be sufficient to ensure compliance. The lack of detailed auditing, insufficient data protection measures, and the inability to enforce least privilege on a granular level can leave gaps in compliance and governance frameworks.
Privilege Access Management (PAM)
PAM secures, controls, and monitors access to an organization's critical information and resources by managing elevated access and credentials. It involves the use of policies, technologies, and controls to protect privileged accounts and prevent unauthorized access or misuse.
The Complementary Role of PAM in Enhancing IAM
PAM steps in to address the shortcomings of IAM by focusing on the most sensitive accounts within an organization—privileged accounts. These accounts are often targeted by cyber attackers due to the unrestricted access they can provide to an organization's critical systems and sensitive data. PAM solutions are designed to secure, control, and monitor access to these high-risk privileges, ensuring that only authorized users can access them, and only under the right conditions.
Enhanced Security Through Privileged Session Management
PAM enhances IAM by introducing privileged session management, which goes beyond static role definitions and permissions. It provides a more dynamic and context-aware approach to access control. For instance, PAM systems can enforce multi-factor authentication (MFA) for privileged users, require approval workflows for access requests, and offer session recording capabilities. These features ensure that every privileged session is authenticated, authorized, and audited in real time. Session recordings and keystroke logs also provide a forensic trail that is invaluable for investigating security incidents or breaches.
Least Privilege and Zero Trust Principles
PAM operates on the principles of least privilege and Zero Trust, ensuring that users have only the access necessary to perform their job functions and nothing more. This minimizes the attack surface by reducing the number of users with always-on privileged access and, instead, grants privileges on a need-to-use basis with JIT access. By integrating with IAM, PAM can leverage existing identity information to streamline the process of granting and revoking privileges, thus maintaining a seamless user experience while enhancing security.
Conclusion
Together, IAM and PAM create a layered defense strategy that is more robust than either solution alone. IAM lays the groundwork for user identity management and basic access control, while PAM builds upon this foundation with advanced measures for the highest-risk access scenarios. This complementary relationship not only solidifies an organization's defenses against external threats but also provides a comprehensive framework for governance and regulatory compliance.


 SOC2 Type II
SOC2 Type II